WireGuard is a modern VPN protocol known for its simplicity, efficiency and strong security features. Its lightweight design ensures minimal resource usage and high performance, ideal for both low-powered devices and high-speed networks. With support for dynamic routing and modern cryptography techniques, WireGuard offers low-latency connections, seamless cross-platform compatibility, and active community support. Think of WireGuard as your exclusive internet hideaway, ensuring swift and secure browsing that’s just for you. Its ease of use and reliability have garnered excitement among users worldwide.
In this guide, we’ll walk you through the process of setting up WireGuard VPN on Ubuntu 22.04 step-by-step. By the end, you’ll have a secure and efficient VPN connection to protect your online activities.
Prerequisites
Before proceeding, ensure you have:
- Ubuntu 22.04 system with root or sudo privileges.
- Basic Knowledge of Linux Commands and Networking Concepts.
Installation of WireGuard
Here’s the step-by-step guide to installing WireGuard on Ubuntu 22.04.
Step 1: Update and Upgrade the Packages. *** Upgrade is Optional ***
sudo apt update -y
sudo apt upgrade -y
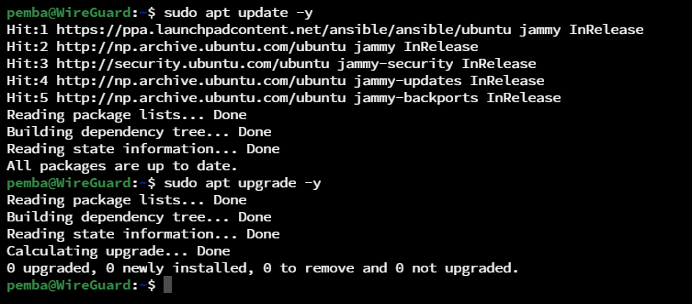
Note: -y to automatically answer “yes” to any confirmation messages that appear during installation process.
Step 2: Installing WireGuard
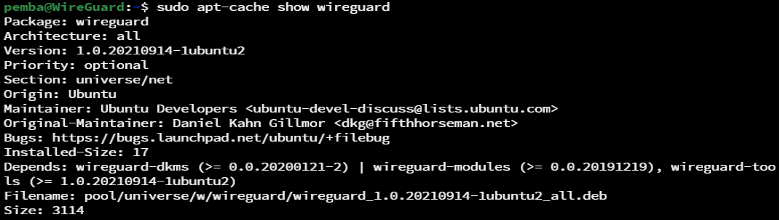
To search packages that provides wireguard, run the command below:
sudo apt-cache show wireguard
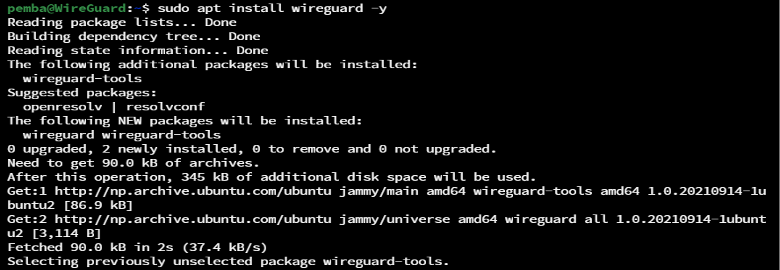
Run the following command to install wireguard
sudo apt install wireguard -y
Step 3: Verify the installation
List packages installed on the system
dpkg -l wireguard
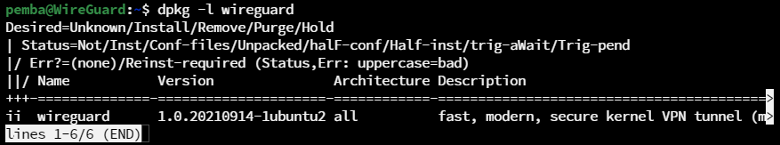
Now, the WireGuard packages are successfully installed on our system and are ready for configuration on your Ubuntu 22.04 system.
Configuration of WireGuard
Generating Public and Private keypair for the Server. (These keys are essential for securing you VPN tunnel.)
wg genkey | sudo tee /etc/wireguard/private.key
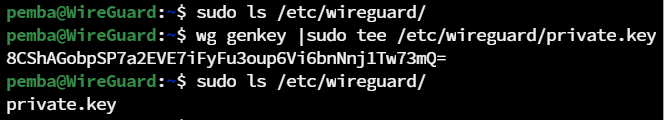
For Viewing the file permissions
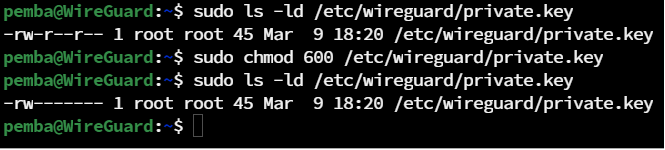
sudo ls -ld /etc/wireguard/private.key
Change the file permissions
sudo chmod 600 /etc/wireguard/private.key
Get the public key from the previously generated private key and save it to a file.
sudo cat /etc/wireguard/private.key | wg pubkey | sudo tee /etc/wireguard/public.key
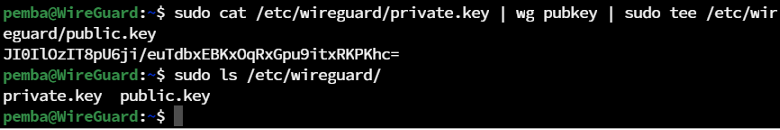
Note: Copy this Public Key. You will need to provide it to clients that need to connect to the server.
Step: 5 Configuring WireGuard
Add following lines on /etc/wireguard/wg0.conf file
sudo vim /etc/wireguard/wg0.conf
[Interface]: defines settings of WireGuard interface on server
[Peer]: defines settings for a peer (client) that will connect to your WireGuard Server.
PostUp runs when the WireGuard server starts the virtual VPN tunnel.
PostDown runs when the WireGuard server stops the virtual VPN tunnel.
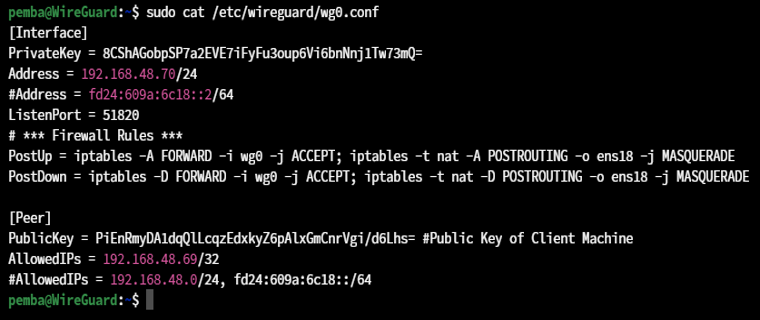
Note: You can also use IPv6. Add an Address parameter again in the [Interface] section, and you can add client range IPs by including client IPs in the AllowedIPs parameter in the [Peer] section, separated by commas.
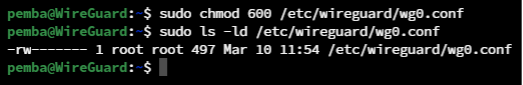
Changing the File Permissions:
sudo chmod 600 /etc/wireguard/wg0.conf
sudo ls -ld /etc/wireguard/wg0.conf
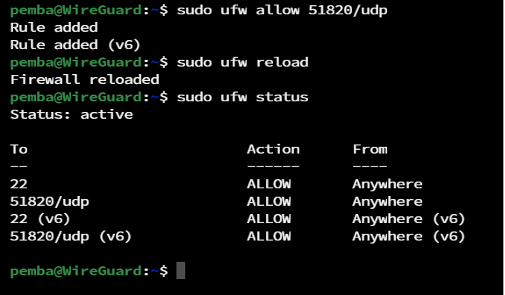
Allowing port from firewall:
sudo ufw allow 51820/udp
Reloading Firewall:
sudo ufw reload
Viewing status of firewall:
sudo ufw status
Step 6: Enabling IP Forwarding
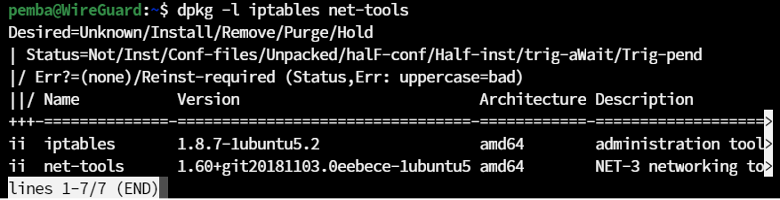
sudo apt install iptables net-tools -y
Verify the installation:
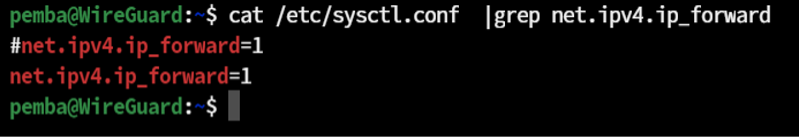
To enable IP forwarding, Find the line #net.ipv4.ip_forward=1 and uncomment it
sudo vim /etc/sysctl.conf
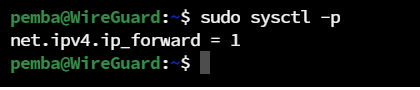
To verify the Configuration:
sudo sysctl -p
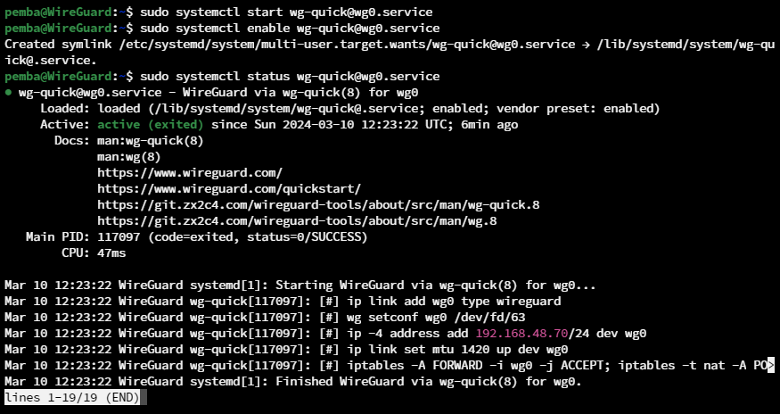
Step 7: Start and Enable the WireGuard Service
Starting the Service:
sudo systemctl start wg-quick@wg0.service
Enabling the Service, to auto active if server rebooted:
sudo systemctl enable wg-quick@wg0.service
Viewing the server status:
sudo systemctl status wg-quick@wg0.service
Now, there’s additional interface is displayed on your machine. You can verify by ip link or ip a command:
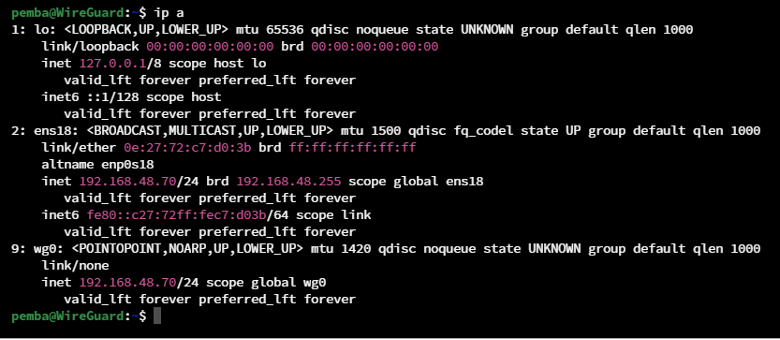
Step 8: Viewing interface configuration and state
sudo wg show wg0
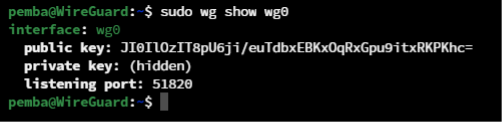
With this, the server configuration is complete! Now, let’s proceed to configure the client machine to test the WireGuard Server.
Configuring Client Machine
To configure the WireGuard client on the Ubuntu machine, follow these steps:
Step 1: Install WireGuard
sudo apt update -y
sudo apt upgrade -y
sudo apt install wireguard -y
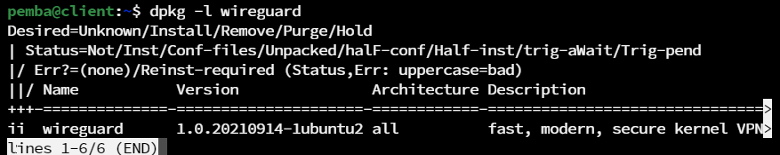
Verify the Installation:
dpkg -l wireguard
Step 2: Generate a Private and Public Keys (just like on server)
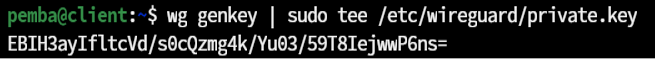
wg genkey | sudo tee /etc/wireguard/private.key
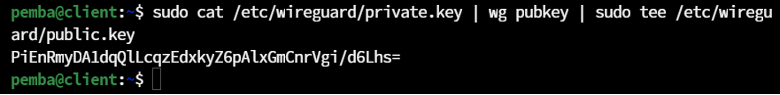
sudo cat /etc/wireguard/private.key | wg pubkey | sudo tee /etc/wireguard/public.key
Step 3: Creating Client Configuration file
Just like, we did in server:
sudo vim /etc/wireguard/wg0.conf
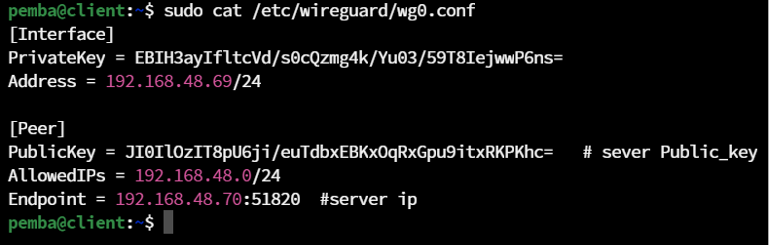
Note: The PrivateKey is the key generated on the client machine, while the PublicKey is the key generated on the server.
Step 4: Start and Enable a WireGuard Service on Client Machine.
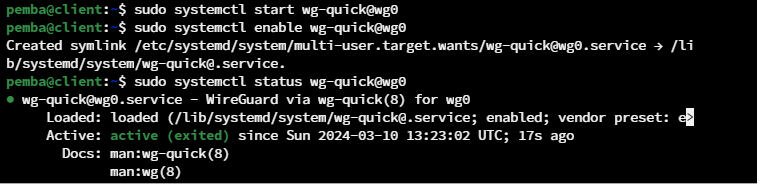
sudo systemctl start wg-quick@wg0
sudo systemctl enable wg-quick@wg0
sudo systemctl status wg-quic@wg0
Step 5: Update the server peer configuration.
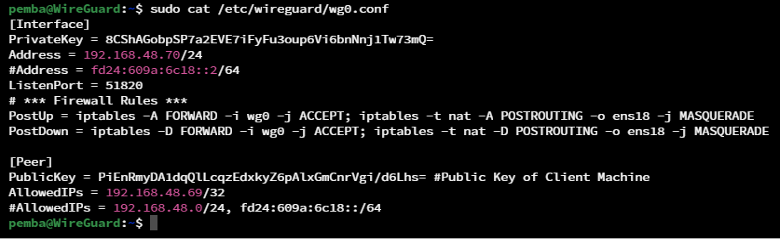
Step 6: Restart the VPN Server
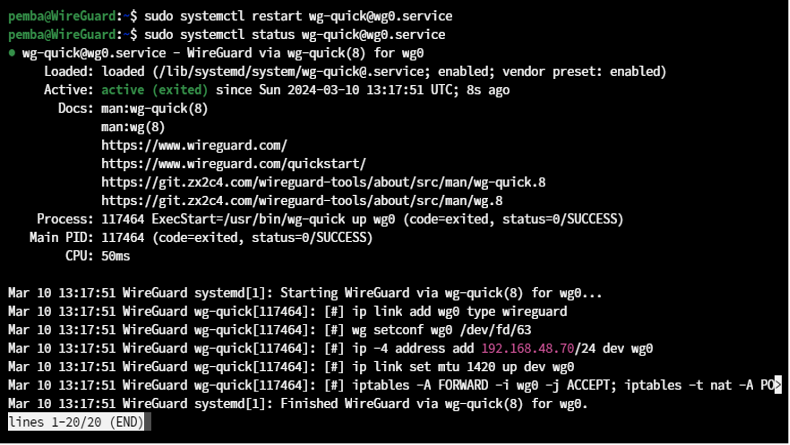
sudo systemctl restart wg-quick@wg0.service
sudo systemctl status wg-quick@wg0.service
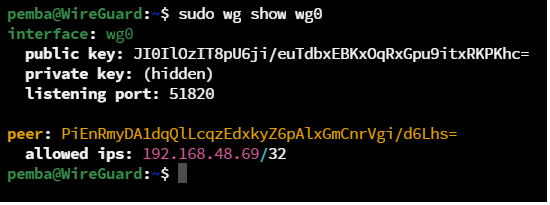
Step 7: Verify the Connection On Server Machine
sudo wg show wg0
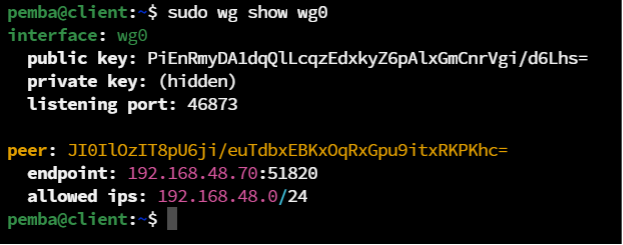
Step 8: Verify the Connection On Client Machine
sudo wg show wg0
Conclusion
This output confirms that the client is connected to the server at 192.168.48.70 and is allowed to communicate with any IP address within the specified subnet.
In conclusion, configuring WireGuard VPN on Ubuntu 22.04 is a streamlined process that provides enhanced security and privacy for your network communications. By setting up WireGuard, you ensure a robust and efficient VPN connection between your server and client machines. With its simple configuration and powerful encryption, WireGuard offers peace of mind while maintaining high performance. Embrace the simplicity and effectiveness of WireGuard for a secure and seamless networking experience on Ubuntu 22.04.